How to Identify Which Products to Select on the SUP/WSUS Products tab
Date Created: Apr 06, 2022 (UTC)Last Updated: Nov 21, 2023 (UTC)
Have you ever wanted to know which Configuration Manager Software Update Point (SUP)/WSUS products you should enable so your devices receive all available patches?
An easy way, but definitely not recommended, would be to enable all products. This is a bad idea as workstations would have to download a large amount of metadata and that would impact the scanning process.
Before today, there was no easy way to identify which products to select. You could go through all of the software titles in your environment, and then try and figure out which products they match to. Or you could just know your environment well enough to know which ones to select.
As an Architect for a global MSP, I routinely go into environments I have no knowledge of. Verifying they have all the required products selected is a task I cannot do without extensive data gathering. I searched the internet looking for an easy way to identify which products should be selected, but found none. I even posted in online forums, but no one was able to provide an answer.
After doing some more research, I devised a PowerShell script that can identify which products each device needs updates for.
Using the Microsoft.Update.Searcher COM object, the PowerShell script goes online and scans directly against Microsoft Update.
NOTE: The script DOES NOT install any updates it detects, it just scans for them.
The results of the scan are then parsed and the products related to the updates Microsoft identified are captured. Optionally, the results will be loaded into a custom WMI class so they can be inventoried by MECM/SCCM. By default, the WMI class is called Update_Product_List and it is found under the ROOT\ITLocal namespace
Update Nov 21, 2023: Additional logic has been added to the script to work around an issue introduced by the 'Specify source service for specific classes of Windows Update' GPO setting. That GPO caused no results to be returned by the query if the source was set to Windows Server Update Services.
Once the Hardware Inventory classes are extended to inventory this information (not detailed here), you can report against those metrics. I created a report that compares the products devices have installed, with what is selected on the Products tab of the SUP. I've included the report, along with the script, in the download at the end of this post.
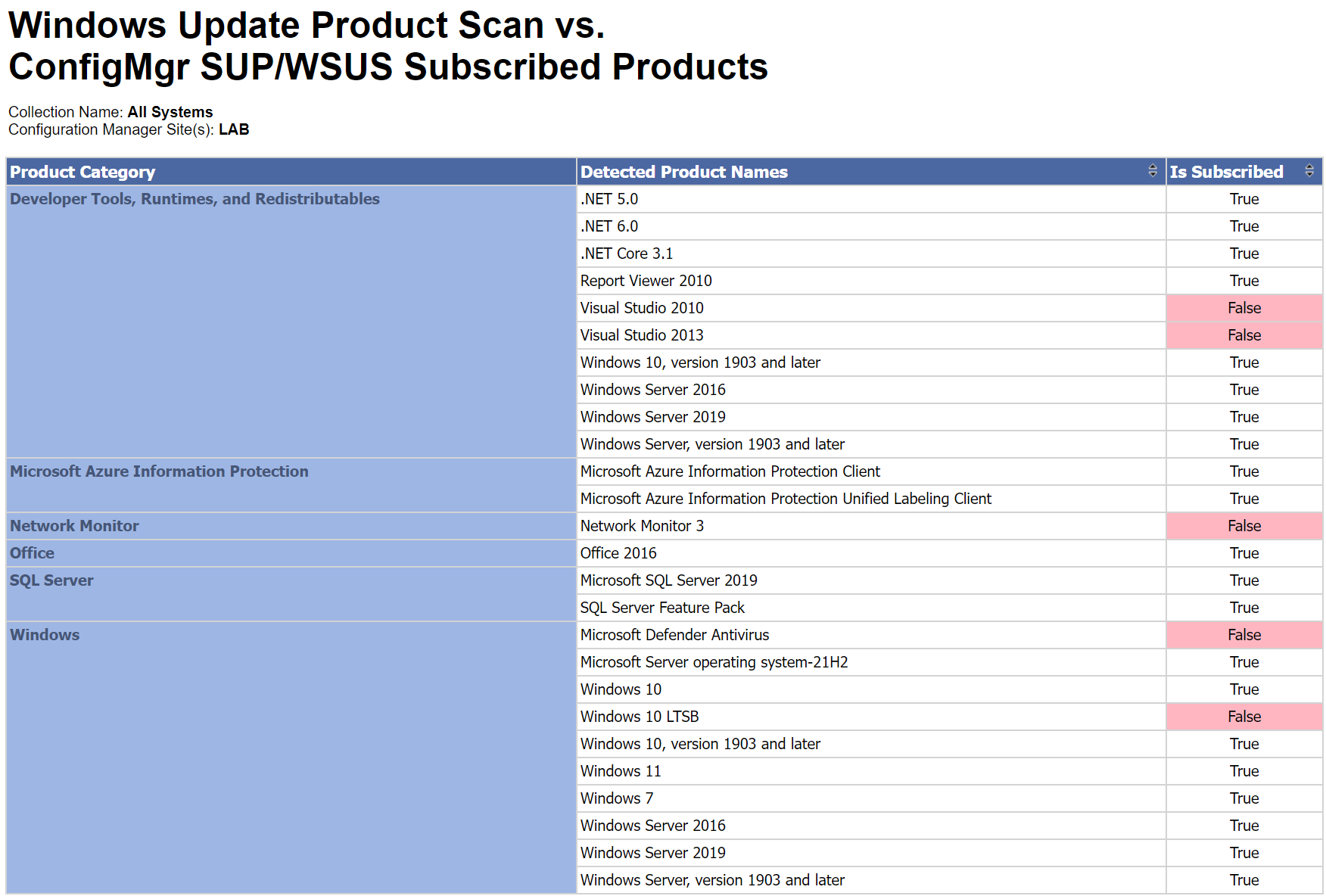
The report is Collection based, and will only show products that pertain to the devices in the collection. This way you can make sure your ADR's have all of the products selected for the devices you are targeting, and not have them scan for products that the devices don't have installed.
You may also see Windows versions and Products that are not in your environment. For example, in my lab, it is showing 'Windows 10 LTSB' as a product found on a device, but in reality, I do not have LTSB installed anywhere. What is happening here is that some updates, like the monthly CU, apply to multiple products, and all of those products will be included by the scan.
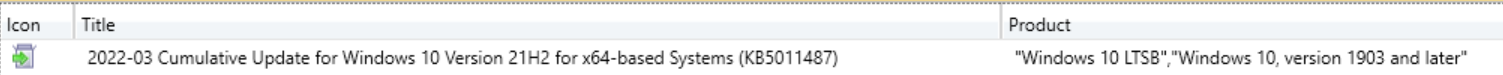
At this point it is important to point out what needs to be enabled for the script to work.
The devices MUST be able to communicate with Windows Update (download.windowsupdate.com) to get metadata. If your company blocks access, then the script won't work.
You can check if you can communicate with Windows Update by going into Settings and clicking on Update and Security. If you see the link 'Check online for updates from Microsoft Update.' you should be good to go.
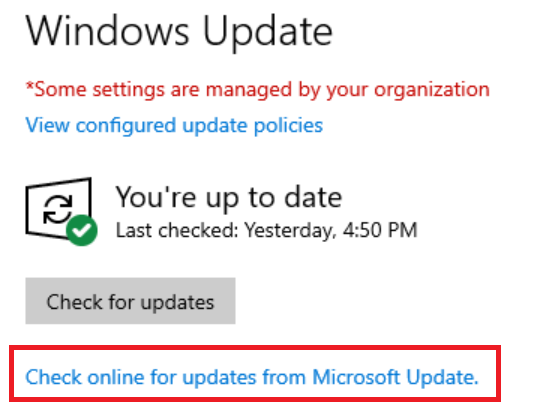
If you do not see the link, more than likely it is being blocked by the following GPO setting
Computer Configuration/Administrative Templates/System/Internet Communication Management/Internet Communication settings
Turn off access to all Windows Update features = Enabled
The script also requires that 'Give me updates for other Microsoft products when I update Windows' under Advanced Options is enabled.
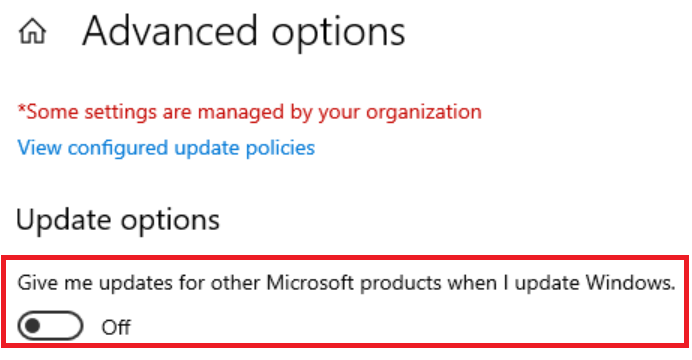
No worries if that option is not enabled. The script will turn it on if it is not enabled, and then turn it back off when done scanning. If it is already enabled, the script will not touch the setting.
The script creates the following three files in C:\Windows\CCM\Logs.
- Get-UpdateProductList.log - The log file for the script itself
- UpdateProductListScanResults.csv - A list of all the updates Microsoft identified that were applicable to your device. It includes whether they are installed or not and what product categories they belong to.
- UpdateProductListProductsFound.txt - Contains a distinct list of products that were found. This is the information that is loaded into WMI.
During my testing I noticed that 'Microsoft Edge' was not reported by any device. I'm assuming this is because Microsoft Update doesn't scan for that since Edge updates itself.
Note: If you use the script to identify which products to unselect, keep in mind that not all products in WSUS may be scanned against Microsoft Update. Before unselecting a product, filter by the product in the ConfigMgr console and if any update shows Required or Installed, don't unselect it.
As always, test, test, test before putting into production.
Download: GetUpdateProductList.zip
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.





Darren DeHaven
12/7/2022 6:48:03 PM (UTC)
Scott Fairchild
12/8/2022 12:27:14 AM (UTC)
Darren DeHaven
12/7/2022 11:13:39 PM (UTC)